 15th December 2017
15th December 2017
The recent much publicised cyberattack on the shipping industry has awoken the transportation sector in general to this salient point: ignore cybersecurity at your peril. The dislocation and economic fallout from the NotPetya attack has undoubtedly acted as a ‘wake-up call’ to how best contain this ever-increasing threat.
Despite the increased threat level, it seems not everyone is taking matters seriously. At a recent shipping conference held in Singapore, the US Coast Guard warned that unless the industry takes the issue more seriously, governments would be forced to introduce regulation.
Evidence suggests the threat has multiplied and will be an increasing burden to business. Cybersecurity Ventures predicted in a report in 2016 that damages from cybercrime will add US$6tn in costs to the global economy by 2021. The recent attack on Maersk incurred up to US$300m in lost revenue, as reported by The Financial Times.
But for Jan Waas, Chief Information Officer, Information Technology of Hutchison Ports, there is no doubt that lessons from recent attacks are crystal clear. He stressed, “What we have learnt from this recent attack is you cannot be sure anymore; you really should accept the fact that security measures won’t stop all attacks. Just one mistake out of a million and a hacker is in. Therefore, you must now go to some sort of operational excellence on all these things and do a one hundred percent check.”
“Even with a one hundred percent check, resourceful hackers may still manage to breach your network,” Wass added.
He stressed, “So enterprises should still establish a comprehensive cyber incident response and recovery capability. They should have a Business Continuity Plan and a Disaster Recovery Plan in place.”
He did not mince his words, “I think with IT security and cybersecurity, you must act with brute force, like shock and awe, and take it seriously. It is no good knowing about a threat but not acting on it. It is about execution of precautionary measures in a real-time manner.”
He suggested businesses now need to allocate more time to this issue. He added, “Yes, perhaps paranoid to the threat and perhaps exaggerated in your acting.”
Recent developments have heightened the threat level. Most significantly, the onset of computing as the primary means of communication is a doubleedged sword. It has brought great benefits in business and personal lives, but this technology has exposed many commercial enterprises to increased security and commercial threats.
According to The Economist, the exponential increase in speed, scalability and efficiency of computers over many decades has undoubted advantages, but its increased complexity, with millions of lines of code, means additional risk: one coding error could wreak havoc on an operational system.
Waas explained, “But the positives outweigh the negatives, we embrace these technologies, we cannot live without the Internet anymore, we do not want to get rid of email or online banking. These things give more prosperity but there are risks; which you must contain.”
This increased prominence of technology in many areas will without question multiply the vulnerability to an attack and increase the opportunity for computer hackers to infiltrate a wider variety of devices, such as smartphones, the Internet of Things (IoT), and even your home camera, according to Waas.
Waas explained, “These emerging technologies have their inherent risks, so you may want to develop targeted countermeasures when you deploy these new technologies to tackle the technology-specific risks”.
This echoes a report entitled ‘Cybersecurity Onboard Ships’ which highlighted how “the growing use of big data, smart ships and the IoT will increase the amount of information available to cyber attackers and the potential attack surface to cyber criminals. This makes the need for robust approaches to cybersecurity important both now and in the future.”
One critical insight is that ships can be particularly vulnerable to an attack, as multiple stakeholders involved in the chartering of a ship can result in a lack of accountability for the IT infrastructure, the report intimated.
Waas backed up these findings and issued a warning of an imminent attack. He stressed, “The more devices getting connected ramps up possibilities for weaknesses. You cannot prevent attacks. They will happen, it is just a fact of life.”
Ultimately, this means almost any individual or organisation can be a target. The interconnectedness of computers is the root factor behind its vulnerability and this has profound implications. It means threats such as ransomware need not target mission critical
systems, as pointed out by Professor Kai-Lung Hui, Deputy Head and Chair Professor, Department of Information Systems, Business Statistics and Operations Management, School of Business and Management, Hong Kong University of Science and Technology.
Ransomware often entices users to unwittingly click on emails with corrupted files to download that can then wreak havoc across an entire system, insisted Hui. In these types of attacks hackers create encrypted copies of files before deleting the originals and then asking for payment to de-encrypt the data. According to a prominent security negotiator, coughing up and caving in to hackers’ monetary demands will place the targeted company on a blacklist, vulnerable to future attack, as reported by WIRED.
By way of response to recent cyberattacks, it is known several shipping lines have updated their security systems and have installed multi-layered protective systems. However, a report by leading market intelligence provider SeaIntel revealed almost one half of container carriers have a worrying low level of protection against cybercrime.
Further to this revelation, the fact that there have been few reported high-profile cybersecurity attacks in the logistics sector does not warrant complacency, according to Hui.
He stressed, “The lack of incidents does not mean that the logistics sector is not a high-risk group. Quite the contrary, I think its fundamental risk is high because of its heavy reliance on information.”
Hui wrote a major report on cybersecurity. He maintains that any organisation that heavily utilises information in its operation or decision making is a potential target. Individual researchers at his university had been targeted and his colleague had fallen victim to ransomware.
He added, “The logistics sector relies on timely and accurate information for coordinating its activities. Hence, the threat is imminent.”
A recent high-profile data breach on a major US information company that trades on personal information underlines the vulnerability of IT systems in many major businesses. The Economist suggests concerns are being raised that if an operation whose raison d’etre is managing data can be so vulnerable, then nowhere is safe.
To best protect against cyberattack, Jan Waas insists systems should be designed with security in mind from the outset, and in the light of recent attacks this requirement is even more critical as the risk perspective has moved up several notches.
He explained what action needs to be taken, “It is a thousand things to be honest – especially designing the systems with security in mind. It is called security by design and applying a lot of technology. Encryption, firewalls and so on; every mature or professional company is up to that standard to a certain extent.”
Waas stressed, “Effective firewalls, which establish barriers between different networks, and different layers of protection are needed. The key point about IT security is you never know where there is a weakness and it will never be one hundred percent solved in the technology only.”
He added, “It is about applying a lot of measures across different systems and also creating awareness across the entire organisation.”
MAJOR INDUSTRY REPORT ON CYBERCRIME
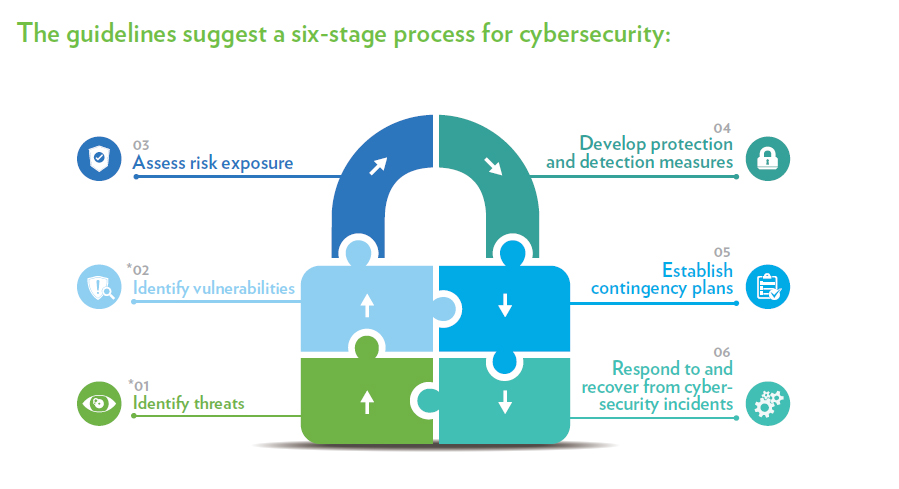
‘Cybersecurity Onboard Ships’, backed by heavyweight organisations in the shipping industry, including the Baltic and International Maritime Council.
Offering practical advice and management best practice on cybersecurity and cyber safety-related matters, the guidelines in the report are further aligned to recent research and recommendations published by The International Maritime Organisation (IMO).
Recent major global cyberattacks such as the ransomware called WannaCry, which infected hundreds of thousands of computers worldwide with outdated Windows operating systems, have heightened the levels of awareness of the menace posed by hackers.
This is especially the case since many companies suffer collateral damage from attacks that originally target other companies or even industrial sectors.
Pertinently, Waas conceded that every IT measure has a loophole. However, the way the systems are meshed together with organisational and individual awareness should then eliminate these loopholes. It is imperative to have a restoring strategy to restore your systems and data were these loopholes to be breached.
However, the threat level has undoubtedly increased over recent years in its intensity and sophistication.
Hui explained, “Cyberattack evolves over time and today the hacking profession has transformed in such a way that hacking has become much easier and accessible. There are now hacker-as-a-service and hacking tools such as ransomware that are easily downloadable.”
He added, “Underground black markets are abundant too. These imply that attacks can come from anyone and anywhere, meaning the industry must conduct a thorough assessment on the potentially vulnerable points in their systems, including the desktop computers of everyday workers. Security threats resulting from human error is one major factor constantly mentioned by companies in survey after survey.”
This is partly down to social engineering motivating many hackers, where personal security information is the desired objective. In many instances, IT system disruption is not obtained by hacking into a system, but by securing a user account and password, often via phishing emails.
Waas explained, “It is amazing how sophisticated these things are. If you project it to a house. They don’t want to break into your upstairs window they just want to copy your key. They try to get your key by getting your password, and if they have your password, then they can create mischief.”
Waas went on, “So, the whole thing is keeping up your systems, keeping up your password security levels, setting up the right defences, which are all standard practice for any organisation.”
This raises an issue that needs to be addressed for many companies involved in shipping and logistics: administrative rights or access rights to emails and the connectivity of all the IT systems.
Waas suggested, “A good network segmentation between the operational processes and administrative processes is needed. And these days the more sophisticated building and equipment automation needs to be reviewed and, if necessary, carefully segmented. It is about creating a more secure environment. Everything gets connected: computers operational across offices; to equipment utilised in the business; through to sensor devices in the operational process; even smart phones of people in the organisation.”
Under this present-day scenario where access to company emails is almost universal amongst many company employees, Waas intimated that additional authentication requirements should be introduced.
He warned, “It takes just one person to click on an infected email and a virus can enter your company. Therefore, it makes sense to review access to emails.”
He feels there is a need to coordinate a response to the threat as “the more information you can share the more you can understand the future direction of threats going around.”
Another major concern is legacy IT systems from the late 1990’s which were designed with a different configuration. Nowadays, security by design and application of standard industry best practice are key risk prevention requirements.
Moving forward, the two overriding priorities for Waas are execution of best practice and awareness. “The concept of best practice is fine but do you really act on it? Execute it as if it is a standard, the next day you must benchmark it.”
“The other key point is creating more awareness of the potential for these incidents. It is psychology of people, the mindset that makes the difference; the psychology that something will never happen to you. But it will!”
It is this lack of awareness that most concerns Professor Hui. Cyberattacks fall into the highimpact, low-probability (HILP) category, and an influential report produced by Chatham House, a UK-based think tank, argued many businesses remain insufficiently prepared for such events. That was a few years ago and Hui thinks many businesses remain woefully complacent. Furthermore, he insisted, and echoing a point raised by Jan Waas, the risk is escalated as many critical infrastructure or rudimentary services are also digitised and supported by computer systems.
He explained, “Firms tend to underestimate the impact while recognising the fact that the probability of being hit is small. Taken together, they tend to under-invest in cybersecurity protection or insurance.”
On an optimistic note a major piece of research undertaken by Professor Hui on the Convention on Cybercrime revealed that concerted international effort can deter hackers. However, non-participating countries experience increased attacks. The implication is that hackers strategically choose targets to minimise their own penalty. In the light of these findings, Professor Hui urges governments to work together to combat this threat.
The main findings of his report imply “attackers in cyberspace are rational, motivated by economic incentives, and strategic in choosing attack targets.” However, the evidence is inconclusive whether sharing threat intelligence or software vulnerability within an industry or at government level is effective in mitigating cybercrime.
For Jan Waas of Hutchison Ports it is a balancing act between the security risk versus the operational side of a business. The key point is to be constantly vigilant to future threats.